XSS (Cross-Site Scripting) is a security bug that allows hackers to embed malicious code (javascript) on another website.
This is one of the most common security flaws on Web sites. Systems from large to small such as Facebook, Twitter, … have been subjected to this error. Due to its popularity and danger, XSS is always honored to be in the top 10 most dangerous security flaws on OWASP (Open Web Application Security Project).
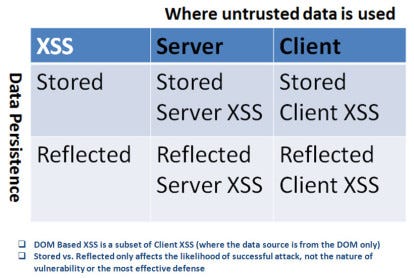
Types of XSS
Previously, XSS often targeted HTML rendering code from the server-side, we called Server XSS. Two common types of XSS Server are Persistent XSS and Reflected XSS.
Here, I will take a young man named K as an example.
1. Persistent XSS
On forum p**hub, when you post a comment to the topic, the server will save the comment you post and display it as HTML. When H posts “I want to find JAV,” the server will collect and display the following:
<div class = "comment">
<p> I want to find JA* </p>
</div>However, K is not so gentle. Because I have just learned about XSS, K did not enter text but entered the script alert (‘XXX ‘) into the comment box. At this point, the webpage’s HTML will become:
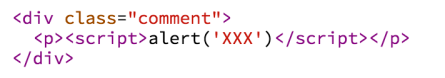
The browser will run this script, displaying an alert window. K has inserted malicious code into p**hub, successfully carrying out an XSS attack. (Note: I just, for example, p**hub does do not have XSS errors, you should not try).
In this type of attack, malicious code is stored in the database on the server, visible to all users, so we call it Persistence XSS.
Anyone who sees the comment of K is infected with this malware, so this type of attack has a significant impact, quite dangerous.
2. Reflected XSS
With this attack, the hacker inserts malicious code into the URL as a query string. When the user ignores the URL, the site will read the query string, render malicious code into the HTML, and the user will be “trapped.”
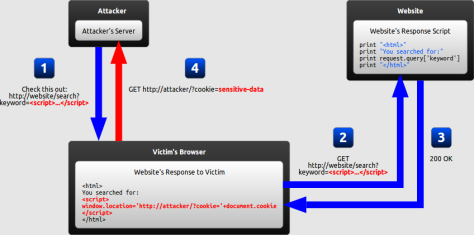
Back to K. Because of asking for an address to massage all the time but not to share, K kept getting angry and decided to get revenge on the seniors. K then sent a fake JAV link to the seniors. Link text: Http://p***hub.com?q= <scrit> deleteAccount(); </scrit>.
When the seniors click this link, they will go to p**hub page. The server then renders <scrit> deleteAccount(); </scrit>, calling the deleteAccount function in JavaScript to delete their account.
The range of ReflectedXSS is not as wide as Persistance XSS, but the degree of danger is equal. Hackers often send malicious links via email, messages, … and entice users to click. So you do not want to JAV link click nonsense,
(Since WordPress automatically filters tag scripts, I have to leave it as a script. Read about “Anti-XSS” below).
3. Client XSS
Recently, as JavaScript became more and more popular, XSS Client errors were also taken advantage of. Because JavaScript is used to process the DOM, malicious code is inserted directly into JavaScript.
Prevention
The principle of the series “Introduction security” is: Hack to learn, not learn to hack. My goal is not to teach you to hack and disrupt other sites but to teach you to know and prevent these attacks.
Because XSS is a typical attack, causing high consequences, most famous Web Frameworks (Spring, Django, ASP.NET MVC) have built-in defenses. Although you are heathen, do not know anything about XSS, just use the latest version of the framework to prevent a lot of bugs already.

This XSS error is also quite easy to fix, this error must be common in many pages, easy to miss, so after fixing, we must verify carefully. There are three commonly used methods to fix this error:
1. Encoding
Do not trust any user input !! Use the encode function available in the language/framework to convert <> characters into < %gt;
2. Validation / Sanitize
Another way to combat XSS is validation: completely remove suspicious characters in the user’s input, or report an error if the input contains these characters.
Also, if you want to allow users to enter HTML, use sanitizes libraries. These libraries will filter dangerous HTML, CSS, and JS tags against XSS. Users can still use the tags <p>, <span>, <ul> to present text.
Please, again, please use the available libraries and don’t “write back” to show proficiency. There have been many cases of XSS errors because developers are confident and write their code to eliminate special characters and … to leave out.
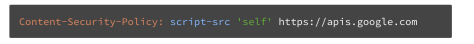
3. CSP (Content Security Policy)
Currently, we can use the CSP standard to combat XSS. With CSP, the browser only runs JavaScript from specified domains. Assuming po**hub.com uses CSP, only run JavaScript that has po**hub.com origin. Because K has malicious code on khoatran.com, the following JavaScipt will not be executed.
<div class = "comment">
<p><script src ="//po**hub.com/poison.js"</script></p>
</div>To use CSP, the server only needs to add the Content-Security-Policy header to each response. Header content contains domains that we trust.
Conclusion
Slightly subjective bit (because I do not like PHP), the number of sites built with PHP XSS error is the most. The first reason is that the number of websites written in PHP is very high. The second reason is that PHP does not encode strange characters by default. PHP CMSs like WordPress, Joomla are very powerful with loads of plug-ins. However, many negligent plug-ins are responsible for this security error.
Currently, the number of XSS website is quite large; you just need to wander online to meet. For ethical reasons, please follow the example of juno_okyo, when you find out, notify the admin so that people can fix it. Don’t play the “young buffalo” hack like me.
As I said, XSS is a significant bug, almost every hacker knows it. This faulty website is easy for hackers. Therefore, the developer you remember to be careful, do not let your website get this error.
Whoever finished the code, then check to see if I’m stuck, whoever is coding is just testing the system. Remember to like and share this article with many developers so everyone can avoid it.
Some reference links:
